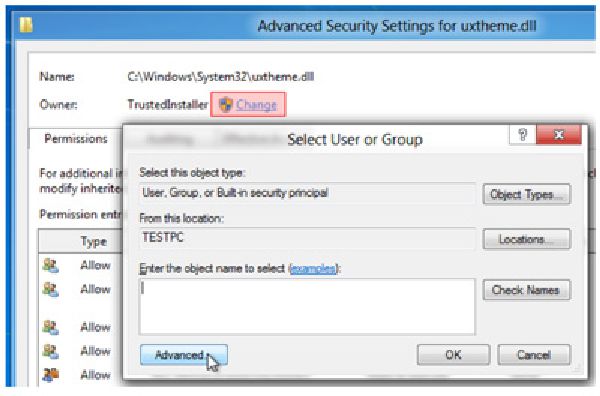
Permissions to Folders Tip !!!
By Krume Stojanovski
At times, you may find you cannot gain access to a certain folder on a hard drive. This may be more of a problem when you install a new Computer, and attached your old hard drive to the new Computer so you can copy the data. In general, the new Computer will treat the old hard drive as a “foreign” drive…

RAM/Memory Upgrade Tip !!!
By Krume Stojanovski
I had attempted to upgrade the Memory on a Dell Vostro 230 Desktop PC, but ran into problems. The Client’s Computer had 2 Gb of Memory (2 x 1Gb), and I attempted to upgrade the computer to 4 Gb (2 x 2Gb). Each time I upgraded (I attempted this 3 times, with 3 different types of Memory...
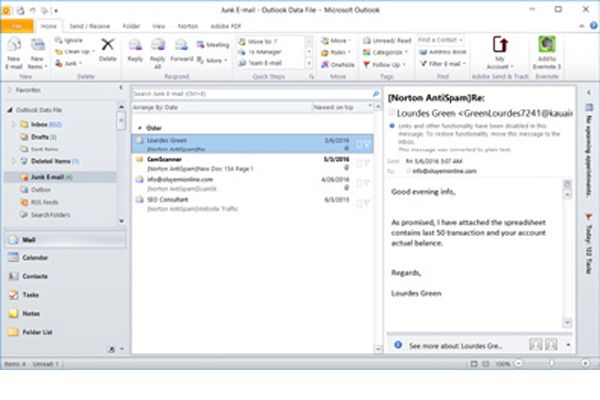
Outlook Moves Most Emails to Junk Folder
By Krume Stojanovski
A client contacted us about a problem he was having with most new emails going directly to Outlook’s Junk Email Folder. At first, it was suspected the client had setup up a faulty rule in Outlook. That was not the case. We reviewed and researched issues with Exchange Server possibly marking these emails as spam...

Phishing and Not Fishing
By Krume Stojanovski
This is an article obtained from another website. While not my own, it is worthy of publishing:
-----------------------
Hundreds of thousands of people received “phishing” emails that appeared to be from the large domain registrar Godaddy...
FOLLOW US